Protecting your assets in the cloud
Securing your business domain needs to be as natural as locking the door and switching on the alarm when you leave. That used to be the basis of security, right?
Nobody gets through a door and onto the premises because there’s a solid barrier backed by an audible alert. And if somebody were to barrel through, then you’d know about it: the alarm would sound and you could then take action. The door and the alarm serve as the deterrent to stop thieves and bad actors from getting your valuables.
In today’s high-stakes digital world, this material security is not enough. Physical entry to your premises is not your biggest concern. Instead, threat vectors manifest online via unmanaged and ubiquitous internet connections and expand via the clouds that you’re using for applications, workloads and storage. And every cloud has multiple entry and exit points or doors.
So with your business driving into the cloud, you’ll have significantly more metaphorical doors through which an intruder could pass, because each cloud vendor that you utilize will have several ways in and out. And the challenge is getting bigger; in a recent cloud security report 76% of respondents have deployed in 2 or more clouds (up from 62% in 2021).
So how can you protect your cloud assets?
Continuing with the analogy of a door, comprised of a set of components that fit together. Each part makes the whole structure – think of the door, its hinges, handles, locks, bolts, keys etc. Without one of these elements your door is not fully operable – the whole is greater than the sum of its parts. Cloud security is the same.
Just like a fully operational door, each element of your security strategy has to fit together and work in unison with other elements. Can you imagine having your doors and alarm fitted by 4 or 5 different contractors, each with separate job sheets? Maybe the cost would be O.K., but what if something goes wrong? Who would you call and who’s to say one contractor won’t blame the other?
What happens if the alarm sounds each time the door is opened legitimately? (What we call false positives). You could find yourself with a lot of problems that need your time and effort to fix.
And what if one component was built with inferior materials, which would impinge on the overall quality – would you know about it before the door falls from its hinges?
As with most things: one piece without the others is not strong enough. Apply that principle to your Cloud Security landscape, where malicious attacks are thriving and doubling year on year, getting more sophisticated with advanced threat vectors.
You need to be sure that the door is fitted properly and has the right support, don’t you?
Oh wait, you also need to remember that door has to be readily opened by people who need to get in. The door can’t encumber the right team from entering or leaving – it must be easy and not slow down the pace of mobility.
It’s a challenge, right? But this is one that we’ve been solving for thousands of customers since we started a decade ago. In our partnership with Check Point, make us do security and provide the tools and skills to make your complete virtual security ‘door’. We can even provide a supporting alarm when security is breached. Our CloudGuard security platform can create the whole ‘door’ for you, but equally, we can just fit a new lock or extra bolt if needed (and this is my last mention of the door analogy!).
Our role as your trusted cloud security provider will help strengthen your Cloud security posture and policy. Our focus is on prevention, rather than detection and containment. We use a comprehensive portfolio that knits together multi-layered security to automate changes and updates, saving time, resources and money. We operate at the forefront of cloud security solving problems and challenges with our deep expertise and experience.
Some of the challenges we’re solving:
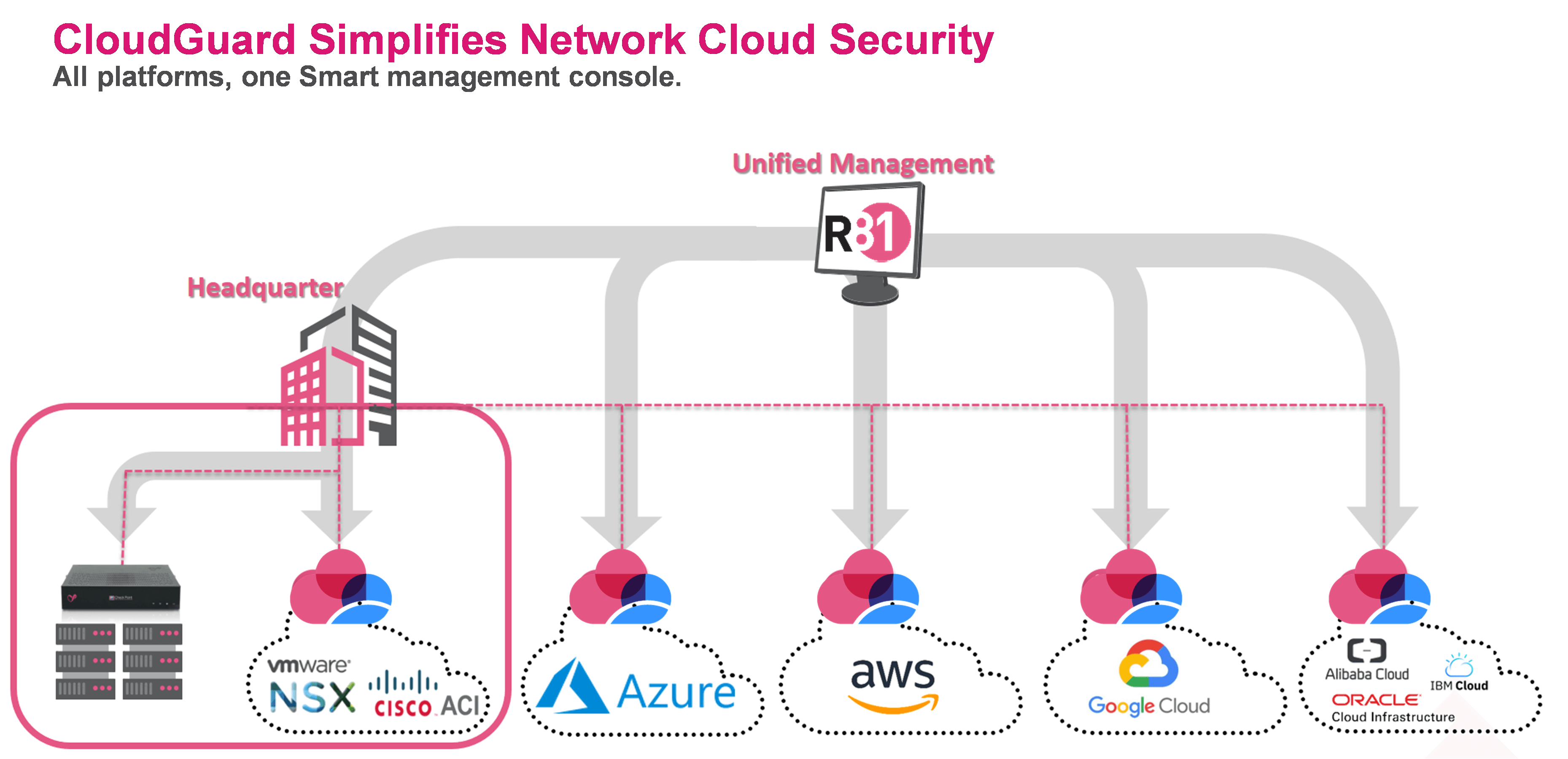
Hybrid Cloud – As per the diagram below, cloud access is direct because sophisticated and virtual security sits in the cloud, and there’s no need to backhaul connectivity for remote sites or users to other security gateways or data centres. You can use scalable virtual appliances in the cloud to extend the same detailed and exact security across all relevant clouds, giving the right performance, scale and support. With one single Smart user console, programmed with a common policy to extend protection across your enterprise. Making growing into the cloud easy, familiar and less risky.
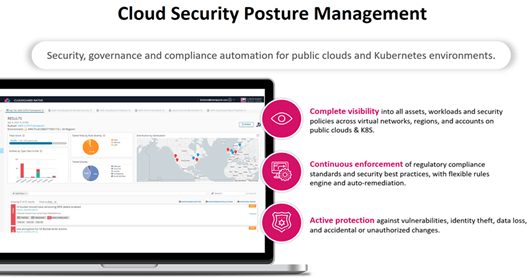
Cloud Posture – When moving or extending in the cloud, the task of keeping track of cloud assets often seems endless. Changes on each cloud, are then multiplied by the number of clouds you utilize and focus on getting everything right time after time. So, adopting a tool that automates this governance across multi-cloud will mitigate risk and save you time. Giving you total visualization and assessment of your security posture and bringing the ability to detect misconfigurations, and enforce security best practices across your compliance frameworks.
Security consolidation – Using multiple cloud security products from various vendors is an approach that leaves organizations with a patched architecture. It increases TCO (spending) and reduces ROI because integration and automation between different vendors’ products become complicated. As a result, the effectiveness of organizational security decreases as more manual labour is needed. Cloud Security unification will yield lower TCO, as stated in this Gartner Article.
In addition, 2022 cloud security reports highlight that 80% of businesses surveyed have to use 3 or more dashboards to configure their enterprise’s cloud security.
See our 2022 Cloud Security report
Security basics
Building a secure cloud blueprint is a key step in your first line of defence. And that means a focus on key elements of your current infrastructure landscape to harden and enforce your weak points. Look for cloud security platforms with a focus on real-time prevention, automation, and unified management – multi-layered protection mechanisms that fully integrate won’t allow attacks to squeeze through gaps.
Ask:
- What visibility and context do you have across your network and cloud assets?
- How are your users aiding or preventing good security?
- What integration is possible with your current security?
- How can DevOps become DevSecOps without losing agility?
- Can you readily apply and enforce uniform policies across all endpoints, and users with differing security products?
- Will I have a single portal for complete management?
Understanding what security you have for the cloud and what you need is a key role for your security team. The trust and reputation of an enterprise largely rest on getting the right IT security posture. Ideally, it needs to be consolidated with your on-premise or branch security on an integrated platform and not spread across multiple vendors. This will undoubtedly aid prevention, lessen gaps and increase the speed of detection. Moreover, it also brings ease of management to growing cloud assets and a quicker return on investment. Allowing you to spend less time and fewer resources managing interfaces, consoles and vendor relationships.
To get you on your way, you can take reach out to our cloud security platform here at ActivEdge Technologies
Need more information about Check Point’s industry-leading cloud security platform, or would like to contact us, or speak with our Check Point account manager please get in touch at https://activedgetechnologies.com/contacts/
Follow and join the conversations about Check Point partnership and CloudGuard on Twitter, Facebook, LinkedIn and Instagram.

